In today’s digital age, where cyber threats are becoming increasingly sophisticated, businesses and individuals alike face significant challenges in securing their digital assets. Sophos, a global leader in cybersecurity, offers a robust suite of solutions designed to protect against a wide array of cyber threats. This comprehensive guide delves into the power of Sophos, highlighting its cybersecurity solutions and firewalls, and how they stand as formidable defenses in the ever-evolving landscape of cyber threats.
Table of Contents
ToggleSophos: At the Forefront of Cybersecurity
Sophos has established itself as a pioneer in the cybersecurity domain, offering an extensive range of products and services tailored to meet the security needs of businesses, IT professionals, and end-users. With a focus on innovation and simplicity, Sophos provides effective, user-friendly solutions that encompass endpoint protection, network security, cloud security, and more.
Sophos Cybersecurity Solutions
Sophos’s cybersecurity solutions are designed with the modern threat landscape in mind, providing comprehensive protection that spans across devices, networks, and the cloud. Some of the key offerings include:
- Sophos Intercept X: A next-generation endpoint protection platform that utilizes deep learning technology to detect and block malware, ransomware, exploits, and zero-day threats. Its capabilities ensure that devices are safeguarded against the latest and most sophisticated attacks.
- Sophos XG Firewall: Sophos XG Firewall goes beyond traditional firewall protection by integrating advanced threat defense mechanisms, such as deep packet inspection, intrusion prevention system (IPS), and advanced threat protection (ATP). This ensures robust security at the network perimeter.
- Sophos Central: A unified console that simplifies the management of Sophos products, allowing for streamlined security administration across multiple environments and devices. Sophos Central enhances visibility and control, making it easier to respond to threats quickly.
- Sophos Cloud Optix: An AI-powered security analytics platform that provides visibility and continuous compliance for public cloud environments. Sophos Cloud Optix helps businesses secure their cloud applications and data against misconfigurations, compliance risks, and cyber threats.
Why Choose Sophos for Cybersecurity?

Choosing Sophos for cybersecurity needs comes with numerous advantages:
- Unified Protection: Sophos offers a synchronized security approach, where different security components work together harmoniously to provide comprehensive protection against complex threats.
- Simplicity and Efficiency: With Sophos, complexity is not a prerequisite for security. The solutions are designed to be straightforward, reducing the operational burden and allowing IT teams to focus on strategic tasks.
- Advanced Technologies: Leveraging cutting-edge technologies like artificial intelligence, machine learning, and cloud-based analytics, Sophos stays ahead of cybercriminals, providing proactive and predictive security measures.
- Global Threat Intelligence: SophosLabs, Sophos’s global threat research center, ensures that Sophos solutions are always updated with the latest threat intelligence, offering protection against emerging and evolving cyber threats.
Implementing Sophos Solutions: Securing Your Digital Frontier
Implementing Sophos solutions across your organization involves a strategic approach to enhance your cybersecurity posture effectively. Here’s a detailed look at steps and considerations to ensure your digital assets are well-protected with Sophos:
Security Assessment:
Begin with a comprehensive assessment of your existing security infrastructure. Identify potential vulnerabilities, assess risk levels, and determine your specific security requirements. This step is crucial in understanding where Sophos solutions can best augment your defenses.
Solution Selection:
Based on the assessment, select the Sophos solutions that align with your security needs. This might include Sophos Intercept X for endpoint protection, Sophos XG Firewall for network security, or other Sophos products that address specific vulnerabilities.
Custom Configuration:
Work with Sophos partners or cybersecurity experts to configure your selected Sophos solutions to meet your unique operational environment. Customization is key to ensuring that the security measures are effective and do not hinder your business processes.
Integration and Deployment:
Seamlessly integrate Sophos solutions into your existing IT infrastructure. Sophos products are designed for easy integration, ensuring minimal disruption to your operations during deployment.
Training and Awareness:
Educate your staff about the new security measures. Training should cover how to use Sophos solutions effectively, recognize potential cyber threats, and follow best practices for digital security.
Continuous Monitoring:
Utilize Sophos Central or other management tools to continuously monitor your systems for threats. Regular monitoring allows for the timely detection of potential security incidents and swift response.
Regular Updates and Maintenance:
Keep your Sophos solutions up-to-date with the latest software updates and threat definitions. Regular maintenance is essential for ensuring ongoing protection against new and evolving cyber threats.
Review and Adapt:
Cybersecurity is an ongoing process. Regularly review the effectiveness of your Sophos solutions and adapt your security strategy as needed to address new challenges and protect against emerging threats.
By following these steps, businesses and individuals can leverage Sophos’s cutting-edge cybersecurity solutions to build a robust defense against cyber threats. Implementing Sophos not only enhances your digital security but also supports compliance with regulatory requirements, protecting your data and maintaining your reputation in an increasingly connected world.
Sophos XG Firewall
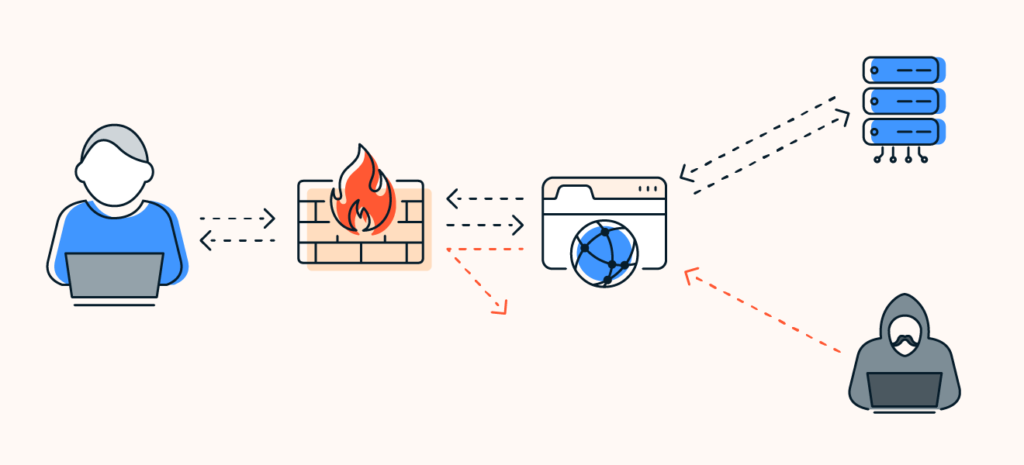
Sophos XG Firewall stands as a cornerstone of Sophos’s cybersecurity offerings, delivering an unparalleled level of protection and intelligence to networks worldwide. This advanced firewall goes beyond traditional firewall capabilities by incorporating a suite of sophisticated security features designed to offer comprehensive protection against a wide array of cyber threats. Here’s a deeper dive into the capabilities and benefits of the Sophos XG Firewall:
1. Advanced Threat Protection
Sophos XG Firewall is engineered with an advanced threat protection system that scrutinizes network traffic for malicious activity. It employs deep packet inspection, intrusion prevention systems (IPS), and an advanced threat protection (ATP) framework to detect and block known and unknown threats before they can infiltrate the network.
2. Seamless Integration with Sophos Ecosystem
A defining feature of the Sophos XG Firewall is its seamless integration with the broader Sophos security ecosystem. This integration enables a synchronized security posture across endpoints and networks, allowing for automatic isolation of compromised devices and coordinated response to threats, significantly reducing the time to detection and response.
3. Sandboxing Capabilities
With Sophos Sandstorm, the XG Firewall offers powerful sandboxing capabilities, providing an additional layer of security. Suspicious files and payloads are isolated and executed in a safe, virtual environment away from the main network, allowing for detailed behavior analysis and threat identification without risking the integrity of the network.
4. Enhanced Visibility and Reporting
Sophos XG Firewall offers unparalleled visibility into network activity with its intuitive control center and detailed reporting features. Administrators can easily monitor network health, user activity, and system alerts in real-time. The firewall’s reporting tools provide actionable insights that help in fine-tuning security policies and identifying potential areas of risk.
5. User and Application Control
Understanding that not all applications and users require the same level of access, Sophos XG Firewall includes comprehensive user and application control features. It allows administrators to set user-specific policies and control application usage across the network, ensuring that only authorized users can access critical applications and data, thereby minimizing the risk of insider threats and data breaches.
6. Web Filtering and Email Protection
To combat the threats posed by web-based attacks and phishing, Sophos XG Firewall incorporates advanced web filtering and email protection mechanisms. These tools block access to malicious or compromised websites and scan incoming emails for threats, significantly reducing the risk of malware infections and data loss.
7. VPN and Remote Access
In today’s increasingly remote work environment, Sophos XG Firewall facilitates secure remote access to the network through its VPN capabilities. It supports various VPN technologies, including IPSec, SSL, and remote Ethernet device (RED), ensuring that remote workers can securely connect to the network from anywhere in the world.
Embracing Sophos and its comprehensive cybersecurity solutions, including the advanced Sophos XG Firewall, equips businesses and individuals with a robust defense mechanism for their digital ecosystem. Sophos not only acts as a formidable barrier against cyber threats but also integrates sophisticated, intelligent security features that safeguard networks from the inside out. By offering peace of mind, advanced threat protection, and seamless ecosystem integration, Sophos empowers users to navigate the digital world with confidence, ensuring a resilient and secure future without the complexity.




